The CSF, or Cybersecurity Framework, was developed by the National Institute of Standards and Technology (NIST) as a guideline to aid organizations in managing and mitigating cybersecurity risks. Initiated by a presidential Executive Order, the first version of the CSF was released in 2014. It provides a set of industry standards and best practices to help organizations manage cybersecurity risks in a structured manner.
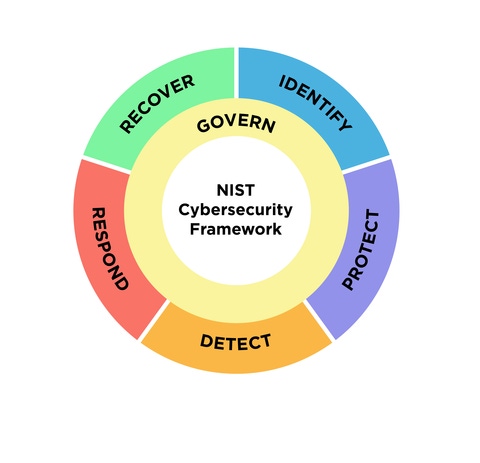
The latest update in February 2024 added a new function, “Govern,” to its core framework, which already included functions like Identify, Protect, Detect, Respond, and Recover, expanding its scope and applicability in addressing evolving cybersecurity challenges.
Let’s break down the 5 key takeaways from this 32-page document:
1) Governance
The most prominent addition to the CSF, Governance refers to the establishing, communicating and monitoring of the organization’s cybersecurity risk management strategy, expectations, and policies. It involves understanding organizational context; establishing cybersecurity strategy and supply chain risk management; roles, responsibilities, and authorities; policy; and oversight of cybersecurity strategy.
Governance activities are critical for incorporating cybersecurity into an organization’s broader enterprise risk management (ERM) strategy. Data governance is part of this category and refers to a set of quality control processes that help organizations in managing, using, improving, maintaining, monitoring, and protecting data.
2) Policy
Policy is a central pillar of governance – an organization must ensure that their security and compliance policies are thoroughly established, centrally managed, and stringently enforced. As the cyber landscape continually evolves, along with organizational missions and technology advancements, it is crucial to conduct regular policy reviews and updates to maintain relevance.
In the context of data security and governance, attribute-based policies can be centrally managed and enforced to automatically allow or deny access to data based on contextual factors, such as the user’s role, location, or the sensitivity of the data.
3) Supply Chain Risks
NIST has placed an added emphasis on managing risks in the global technology supply chain, which involves suppliers, developers, and service providers collaborating across different stages, from research and development to the delivery of products and services. Given the complexity and interconnectivity of these relationships, effective supply chain risk management (SCRM) is crucial for organizations.
By using the CSF, organizations can enhance their cybersecurity risk management and improve communication with stakeholders throughout these intricate supply chains.
4) Emerging Technology Risks
Recognizing the rapid growth of emerging technologies, NIST is now focusing on how advancements like artificial intelligence (AI) introduce new risks that include security and privacy concerns. Addressing AI risks alongside other enterprise risks such as financial, cybersecurity, reputational, and privacy risks is crucial for a cohesive management strategy.
The AI Risk Management Framework (RMF) Core, with its defined Functions, Categories, and Subcategories, provides guidance for managing AI-related risks effectively. This framework is designed to be applicable throughout the entire lifecycle of AI systems, from their initial design and development through to deployment and ongoing evaluation.
5) Applicable to Organizations beyond Critical Infrastructure
NIST’s updated Cybersecurity Framework (CSF) has broadened its scope to assist a wider range of organizations, beyond its initial focus on critical infrastructure. This expanded framework acknowledges the diverse needs and varying levels of cybersecurity experience that organizations bring.
To cater to this range, new adopters have access to a suite of resources, including implementation examples and quick-start guides tailored for different user groups. These resources, which cater to entities like small businesses, enterprise risk managers, and those focused on securing supply chains, provide valuable insights and learning opportunities drawn from the experiences of other users.
Conclusion
In conclusion, the updated CSF 2.0 introduces new areas of focus, from governance to emerging technology risks. For those looking to delve deeper, particularly into effective data management practices, exploring techniques to segregate data logically is crucial. Don’t miss out on gaining further insights – check out our detailed article on logical data segregation to strengthen your organization’s data security strategies.